DVWA Download Crack For Latest Version Of Windows
Web Application DVWA Download Crack is a PHP MySQL 2024
DVWA Download is a PHP/MySQL web application that is damn vulnerable. Its goals are to aid security professionals in testing their skills and tools in a legal environment, to help web developers better understand web application security processes, and to assist teachers and students in teaching and learning web application security in a classroom environment.

DVWA aims to practice some of the most common web vulnerabilities, with varying levels of difficulty, with a simple and straightforward interface. Hence, note that this software contains both documented and undocumented vulnerabilities. This is intentional. We encourage you to try to discover as many issues as possible.
Overview:
Furthermore, DVWA Downloading a vulnerable web application is damn vulnerable! Do not upload it to your hosting provider’s public html folder or other internet servers, as they would be compromised. It’s good to use a virtual machine (such as VirtualBox or VMware) that is set to NAT network mode. It allows users to explore various security vulnerabilities in a secure and controlled environment.
Ryan Dewhurst developed DVWA in 2009. Its PHP and MySQL architecture allows it to be installed quickly on a range of operating systems. You can set up DVWA on Windows, Kali Linux, or even use Docker or VirtualBox. The application provides examples of various vulnerabilities, including brute force, command injection, SQL injection, cross-site scripting (XSS), and more. If you want to learn ethical hacking, DVWA is a great starting point!
Popularization of software and the Internet:
In addition, With the popularization of software and the Internet, people pay more and more attention to web system security. Software vulnerabilities are heavily shrouded in secrecy. Again, Once a web system compromises, it causes incalculable losses to businesses and individual users. Further, How to understand the root causes of various software security vulnerabilities and how to find software security vulnerabilities to improve the security of software systems is a very important topic in software development.
However, DVWA Download can help people understand various software security weaknesses. With DVWA, people can understand the different types of web system security vulnerabilities as well as the different levels of vulnerability prevention methods. Moreover, DVWA aims to practice some of the most common web vulnerabilities, with varying levels of difficulty, with a simple and straightforward interface.
Screenshots:
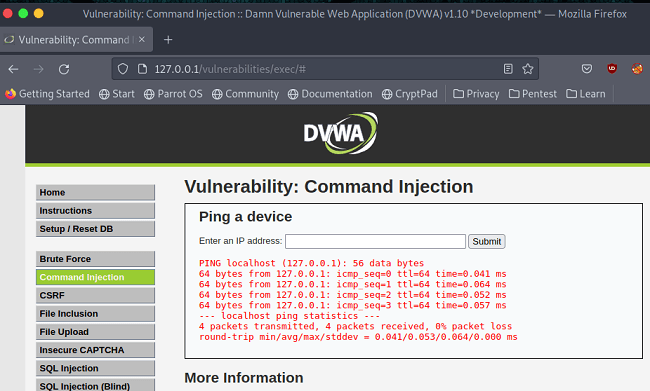
Key Features of DVWA Download:
- Although there are different versions of DVWA, the only supported version is the latest source from the official GitHub repository
- This file is available in multiple languages
- Next, the easiest way to install DVWA is to download and install XAMPP if you don’t already have a web server setup
- However, Depending on your operating system and PHP version, you may want to change the default configuration
- DVWA aims to practice some of the most common web vulnerabilities
How to download DVWA:
This is a Windows application called DVWA. It can be run online with the free workstation hosting provider On Works.
- Download and run this application called DVWA with On Works for free.
- Follow these instructions to run this app:
- You have downloaded this application to your computer.
- Enter the username you want in our file manager.
- Upload this application to such a file manager.
- Run any OS Works online emulator from this website, but use a better Windows online emulator.
- Next, from the On Works Windows operating system you just launched, go to our file manager with the username you want.
- Download the app and install it.
- Download Wine from the Linux distribution’s software repositories. In addition, once installed, you can double-click the app to launch Wine. In addition, you can try Play On Linux, a fancy interface over Wine that helps install your favorite Windows programs and games.
System Requirements:
Here are the system requirements to run DVWA:
- Operating System: DVWA can run on Windows, Linux, or macOS.
- Web Server: You will need a web server like Apache, Nginx, or IIS to host DVWA.
- PHP: DVWA requires PHP 5.5 or higher (PHP 7.x or 8.x is preferable).
- Database: DVWA uses a MySQL or MariaDB database (version 5.5 or higher).
- Browser: You will need a modern web browser like Google Chrome, Mozilla Firefox, or Microsoft Edge to access and use the DVWA.
- Hardware: DVWA can run on a virtual or physical machine with at least 1 GB of RAM and 1 CPU core.
Furthermore, because of its vulnerability, it is crucial to remember that DVWA only serves for testing and teaching purposes. It is not in use in a production setting or accessible to the Internet. As a result, DVWA is known for being easy to use, quick, and adaptable.
What’s new in DVWA Download:
- Improved user interface and navigation
- New vulnerabilities and challenges, including:
- Insecure deserialization
- Password cracking
- Cross-Site Scripting (XSS)
- Cross-Site Request Forgery (CSRF)
- File embedding vulnerabilities
- Enhanced security measures such as:
- Improved password hashing
- Improved input validation and sanitization
- Support for mobile devices and responsive design
- Updated documentation and tutorials
Conclusion:
However, Experimental results show that DVWA provides a testing environment for various web system security vulnerabilities, covers typical types of vulnerabilities, is easy to understand and use, and can help developers improve web system security. However, DVWAs contain mostly different vulnerabilities.
Therefore, when testing a specific web application scanner, it is best to compare the results of the selected scanners with both web application vulnerabilities. Finally, we have the option, It would also be great to test all scanners against real websites, just to be sure one scanner is indeed better than the other. Lastly, Of course, the targeted website should contain at least one vulnerability for the web scanners to find; otherwise, they wouldn’t be able to detect something that isn’t there.